Perancangan Sistem Penyedia File Sharing dengan Enkripsi URL menggunakan Algoritma Rijndael
Abstract
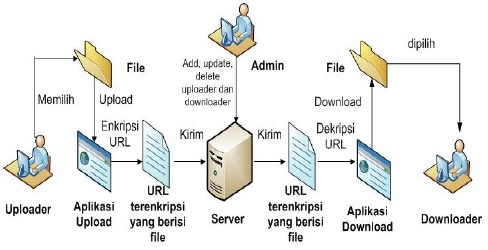
Information in the digital era is growing very fast, seen from the rapid exchange of information. Information in the form of data or text is widely distributed and can be spread easily and quickly through the website. Generally a website uses website-based programming with the GET method where the GET method has a weakness of system data that can be seen in the access directory. This causes the data in the directory can be taken by unauthorized persons. Based on these problems the file sharing system provider was designed with URL encryption using the rijndael algorithm. The system provides services for sharing data and downloading data securely. Between the provider and recipient of the data each has an application that is an application to upload and an application to download and the admin is tasked with regulating the number of users of the application user. Existing data in the URL shared by the user upload application that has been in the form of an encrypted ciphertext with the shared rijndael algorithm can only be downloaded by the download application user. Each application has an authentication process where only registered users can access the application according to their respective roles. Research that has been done to get the results of encryption conducted on the upload application changes the URL into a ciphertext that can only be downloaded using a download application so that weaknesses in the GET method can be overcome.
Keywords : GET method, encrypt, URL, rijndael algorithm, authentication, download, upload ciphertext
Downloads
References
Algoritma Enkripsi AES dan BASE64 dalam Pengamanan METHOD
GET pada URL Website ", Jurnal Manajemen dan Teknologi Informasi
Vol.8 No.2, pp. 66-71, 2018.
[2] I. B. A. Peling, N. P. Sastra, " Enhanced Audio Steganografi dengan
Algoritma Advanced Encryption Standard untuk Pengamanan Data
pada File Audio ", Majalah Ilmiah Teknologi Elektro Vol.17 No.1, pp.
66-71, 2018.
[3] V. V. Deotare, D. V. Padole, A. S. Wakode, "Area and Power Analysis
of AES using Hardware and Software Co-Design" IEEE Global
Conderence on Wireless Computing and Networking (GCWCN), 978-
1-4799-6298-3, pp. 194-297, 2014.
[4] M. Panda, "Performance Analysis of Encryption Algorithms for
Security", IEEE International conference on Signal Processing,
Communication, Power and Embedded System (SCOPES), 978-1-
5090-4620-1, pp. 278-284, 2016.
[5] M. A. Saleh, N. M. Hisham, E. Hisham, H. Hashim, " An Analysis and
Comparison for Popular Video Encryption Algorithms ", IEEE
Information and Communication Technologies 978-1-4799-8969, pp
90-94, 2015.
[6] R. Indrayani, Subektiningsih, P. Ferdiansyah, D. A. Satria,
"Effectiveness comparison of the AES and 3DES cryptography
methods on email text messages", IEEE International Conference on
Information and Communications Technology (ICOIACT), 978-1-
7281-1655-6, pp. 66-69, 2019.
[7] O. G. Abood, M. A. Elsaad, and S. K. Guirguis, " Investigation of
Cryptography Algorithms used for Security and Privacy Protection in
Smart Grid ", Nineteenth International Middle East Power System
Conference (MEPCON), pp. 644-649, 2017.
[8] M. Umaparvathi, D. K. Varughese, "Evaluation of Symmetric
Encryption Algorithms fir MANETs", IEEE Information and
Communication Technologies 978-1-4244-5967-4, 2010.
[9] A. Rahardian, " Implementasi Uniform Resource Locator Encryption
pada Website Berbasis Algoritma BASE64 Studi Kasus pada Pimpinan
Wilayah Aisyiyah Jawa Tengah ".
[10] A. Subari, S. Manan, " Implementasi Aeschipper Class untuk Enkripsi
URL di Sistem Informasi Akademik Fakultas Teknik Universitas
Diponegoro ", Jurnal Sistem Komputer Vol.4 No.2, pp. 63-69, 2014.
[11] I M. A. Bhaskara, I. K. A. Mogi, I P. G. H., 2016 " Perancangan Sistem
Aplikasi Download Manager dengan Enkripsi pada URL menggunakan
Algoritma Blowfish ".
[12] Z. Xinyi, Z. Ru, W. Fangyu, L. Jianyi, Y. Yuangang, "Research on the
Privacy-preserving Retrieval over Ciphertext on Cloud", IEEE 6th
International Conference on Information Communication and
Management, 978-1-5090-3495-6, pp. 100-104, 2016.
[13] G. Wang, C. Liu, Y. Dong, "SafeBox: A Scheme for Searching and
Sharing Encrypted Data in Cloud Applications", IEEE International
Conference on Security, Pattern Analysis and Cybernetics, 978-1-
5386-3016-7, pp. 648-653, 2017.
[14] M. Tanha, S. D. S. Torshizi, M. T. Abdullah, F. Hashim, "An
Overview of Attacks against Digital Watermarking and their
Respective Countermeasure", IEEE Information and Communication
Technologies 978-1-4673-1677-4, pp. 265-270, 2012.
[15] L. A. Tawalbeh, O. Banimelhem, M. Al-Batati, "A Novel High Quality
High Capacity Image Hiding Scheme Based on Image Compression
and an Optical Pixel Adjustment Process", Information Security
Journal: A Global Perspective, 21:256-268, pp. 256-268, 2012.
[16] J. Raigoza, K. Jituri, "Evaluating Performance of Symmetric
Encryption Algorithms ", International Conference on Computational
Science and Computational Intelligence, pp.1378-1381, 2016.
[17] Yogiswara, Wijono, and H. S. Dahlan, "Kinerja Web Service pada
Proses\ Integrasi Data". Jurnal EECCIS 1(1), pp.73-78. 2014.
[18] B. Costa, P. F. Pires, F. C. Delicato, " Evaluating a Representational
State Transfer (REST) Architecture", IEEE/IFIP Conference on
Software Architecture 978-1-4799-3412-6, pp. 105-114, 2014.
[19] Y. Song, "Research on Web Instant Messaging Using REST Web
Service", IEEE Information and Communication Technologies 978-1-
4244-6359-6, pp. 497-500, 2010.
[20] B. Lakshmi, T. N. Prabakar, E. Kirubakaran, "Real time cryptography
with dual key encryption", IEEE Proceedings of the 2008 International
Conference on Computing, Communication and Networking (ICCCN),
978-1-4244-3595-1, 2008.
[21] S. Z.. S. Idrus, S. A. Aljunid, S. M.. Asi, S. Sudin, R. B. Ahmad,
"Performance Analysis of Encryption Algorithms Text Length Size on
Web Browsers", IJCSNS International Journal of Computer Science
and Network Security, Vol.8 No.1, pp. 20-25, 2008.
[22] A. H. Watson, T. J. McCabe, McCabe Software Structured Testing: A
Testing Methodology Using the Cyclomatic Complexity Metric,
Gaithersburg: National Institute of Standards and Technology Special
Publication 500-235, 1996.
[23] N. S. Fitriasari, S. A. Fitriani, R.A. Sukamto, "Comparison of
Weighted Product Method and Technique for Order Preference by
Similarity to Ideal Solution Method: Complexity and Accuracy", IEEE
3rd International Conference on Science in Information Technology
(ICSITech) 978-1-5090-5864-8, pp. 453-458, 2017.
[24] J. L. Anderson Jr., " Using Software Tools and Metrics to Produce
Better Quality Test Software" IEEE Autotestcon 0-7803-8449-0, pp.
293-297, 2004.
[25] A. M. K. Cheng,, "Measuring the Structural Complexity of OPS5 Rule-
Based Programs", IEEE Information and Communication Technologies
0730-3157, pp. 522-527, 1996.

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.

This work is licensed under a Creative Commons Attribution 4.0 International License