Sistem Pengamanan Anonym dengan Menggunakan Algoritma Kriptografi ElGamal
Abstract
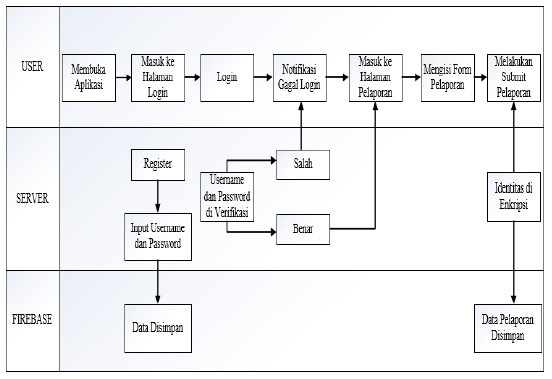
Reporting on act of domestic violence to Integrated Services Center for Woman and Children (Pusat Pelayanan Terpadu Pemberdayaan Perempuan dan Anak (P2TP2A)) Kota Denpasar city is kind of sensitive and vulnerable data to tapping. As a result, security guarantee for the reporter is needed to protect their identity. Security guarantee with anonym reporting system, which uses EIGamal cryptographic algorithm for encryption process and description process. EIGamal cryptographic algorithm is one of asymmetric cryptography which consist of 3 processes, that are process of generate key, encryption process and description process On this security system identity of the reporter will be protected through process of authentication, authorization, and encryption. In this study the researcher uses Android platform and EIGamal cryptographic algorithm for encryption and description, Firebase Auth for authentication, Firebase Rules for authorization and Avalanche Effect for knowing the quality of cryptographic algorithm. The result of the trials which used 10 different ciphet texts of avalanche effect is 58,2%. That result can be categorized as good because a good result of avalanche effect.
Downloads
References
[2] Himawan, Cindy., Wibowo, Toni., Sulistyo, Budi. 2016. Studi Perbandingan Algoritma RSA dan Algoritma El-Gamal. Presiden University.
[3] Sharma, Ankush., Attri, Jyoti., Devi, Aarti., Sharma, Pratibha. 2014. Implementation & Analysis of RSA and ElGamal Algorithm. Asian J. of Adv. BasicSci : 2(3). 125-129
[4] Mulya, Megah., 2013. Perbandingan Kecepatan Algoritma Kriptografi Asimetri. Journal of Research in Computer Science and Applications, Vol.1 No.2
[5] Karima, Aisyatul., Handoko, L. Budi., Saputro, Ari. 2017. Pemfaktoran BilangannPrima padanAlgoritma ElGamal untuk KeamanannDokumennPDF. JNTETI, Vol.6, No.3
[6] Triase. 2015. Kriptografi ElGamal Menggunakan Metode Mersenne. Jurnal Ilmiah “Integritas”. Vol.1 No.4
[7] Kabetta, Herman. 2017. Analisis Kompleksitas Waktu Algoritma Kriptografi ElGamal dan Data Encryption Standard. Jurnal Teknikom. Vol.1 No.1 ISSN: 2598-294X
[8] Parmadi, B. (2017).nImplementasinAlgoritma Kriptografi ElgamalnpadanDatanText, JournalnofnInformationnand Technology, Vol.05 No 01.
[9] Vishwakarma, Manila., Jain Sourabh. (2018). An Efficient Cryptosystem to Perform Encryption and Decryption of Data.
[10] Djellalbia, Amina., Badache, Nadjib., Benmeziane, Souad., Bensimessaoud, Sihem. 2016. Anonymous Authentication Scheme in e-Health Cloud Environment. 11th International Conference for Internet Technology and Secured Transactions (ICITST). 47-52
[11] Nivedita Bisht dan Sapna Singh.. “A Comparative Study of Some Symmetric and Asymmetric Key Cryptography Algorithms”. International Journal of Innovative Research in Science Engineering and Technology Vol. 4 Issue 3. 2015.

This work is licensed under a Creative Commons Attribution 4.0 International License